Safari를 사용하면 '이 연결은 비공개가 아닙니다'라는 메시지가 표시됩니다. 이 웹 사이트는 개인 또는 온라인 결제 정보를 캡처하기 위해 'domain.com'를 가장할 수 있습니다.
ERR_CERT_COMMON_NAME_INVALID is a very popular SSL error during loading the website. In most cases, the issue is due to certificate misconfiguration on a server. However, it may appear due to antivirus and firewall or aother third-party extensions and software. Check the example of the error on the screenshot below.
Fixing the NET::ERR_CERT_COMMON_NAME_INVALID error is not very difficult, but would takes some time and extra steps. You have to start by identifying the cause of mismatch error first.
- AD FS 2.0 receives a signed SAML sign-out request from the relying party. In this scenario, the signout request must be signed. AD FS 2.0 receives a sign-out request from a claims provider, and encrypts a sign-out request for the relying party.
- Show navigation Hide navigation. Home; SSL Certificates. Domain Validation Issued within 2-3 minutes Low trust level. No paperwork D Multi-Domain (SAN) Secure up to 200 domains with one SSL Certificate S Business Validation Issued within 1-3 days.
- That’s it you have successfully Fix Secerrorexpiredcertificate but if you still have any questions regarding this post then feel free to ask them in the comment’s section. Was this article helpful? Related Articles. How To Mute Whatsapp Calls On Android?
- This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which.
Solution 1: Check date and time are proper
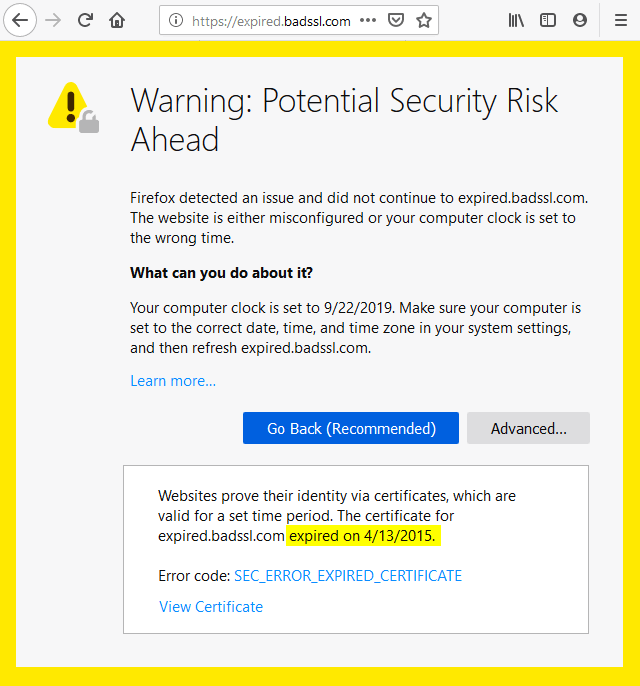
Your Chrome browser will show ERR_CERT_COMMON_NAME_INVALID error in case the date and time are wrong on your computer or mobile device. Please recheck and adjust it on your via PC settings.
Solution 2: Check browser extensions
In some cases, the problematic browser extension could be a reason for the error. First of all, try to open the website in Incognito window and if that solves the issue then no need to check extensions. Otherwise, follow the next steps:
- Click the 'three dots' button on the top right corner of your browser window
- Select More tools and Extensions
- Turn off extensions one by one to find culprit extension and delete it to fix the browser error.
Solution 3: Check Installed SSL certificate
In most cases the issue comes from wrong SSL installed, it may simply not support the correct domain name or sub-domain. That makes a real mismatch result. For example, you issued and installed SSL for www.domain.tld, but installed it for sub.domain.tld which is not protected. You can check that with your browser.
In Chrome, you have to click to the 'Not Secure' button located on the left side of the address bar, and then click to 'Certificate'. There you will see the details of SSL certificate using the field 'issued to'. The feature is available in most browsers.
You can also check that using Online SSL test by SSL Labs, that will be a more accurate result.
Make sure Self-Signed SSL is not in use, as they are used for internal server purposes only.
Solution 4: Protection of both with/without WWW
All Single Domain SSL certificates we sell protect WWW and non-WWW version of your domain name. However, there are some certs that do not protect it by default. In that case, you may have a problem using redirection from WWW to non-WWW or opposite option.
The possible solution is to install a proper SSL certificate or remove any redirect and install Multi-Domain, or Wildcard SSL or even multiple single-domain SSL to protect all domains/sub-domains in use.
Solution 5: For WordPress users
A very popular issue is forgetting to purchase an SSL certificate. WordPress owners enable secures HTTPS protocol for their website without installing or buying SSL, as result they get NET::ERR_CERT_COMMON_NAME_INVALID error message in the browser. There are two possible solutions in that case:
- a purchase an SSL certificate and install it your web server;
- or changing HTTPS back to HTTP to enable your website without any protection and encryption of transmitted data.
Solution 6: Clear the SSL cache
The browser's SSL cache can be an issue. You have to try clearing the cache to resolve the error.
- For IE/Edge. You have to open the Internet properties and find the 'Content' tab, there will be a button to 'Clear SSL state'.
- For Chrome browser the process is similar, click 'Three dots' button on the top right side of the browser, find the 'Settings'. There you will find 'Advanced settings' at the bottom of a page. Now find 'Open Proxy Settings' and there you will see the 'Content' tab with 'Clear SSL state'
Solution 7: Proxy settings
You may have limited browsing experience if Automatical detection of settings is not set via proxy setup. The solution is a Right-click on the Network Access icon to see Internet Properties. Tap on the 'Connection' tab and then to 'LAN Settings'.
You will see a new window where you have to click to checkbox near the 'Automatically detect settings' if it is not checked already. Once done, you can retry opening the website to see if error was solved.
Solution 8: Update OS and Browser
The classical idea is to make sure your OS and Browser is Up to Date as old or outdated software may bring unexpected issues. The developers are working hard to create new patches and bug fixes, so that is critical to have an updated system.
Solution 9: Checking your Firewall/Antivirus
We suggest checking Firewall and Antivirus settings and LOG files to be sure they are not blocking the website you are trying to visit. Review the blocking reason carefully, if you found a block, as probably they are trying to secure you from a malicious website. We do not suggest switching off Antivirus.
Conclusions to summarize
You can clearly see that there are multiple possible issues that may bring you to error FIX ERR_CERT_COMMON_NAME_INVALID. However, it is known error and there are quite easy steps to fix the issue. Check data/time of your PC, browser extensions, try to clean SSL cache, recheck Proxy settings and update OS with Browser to latest versions. That should definitely help. Good luck!
Similar articles from Problems & Issues
Hashing Algorithm – One of the Methods for Sending Essential Files
Moreover, it’s one of the convenient and secure ways when it comes to identifying or comparing databases and files. It’s the process which transforms the dataset into a fixed-length character series, without considering the size of input data. And the received output is known as hash value, digest, code, or simply hash. Additionally, the term “hash” is used for describing both the hash function as well as the hash value.
To put it another way, it’s majorly used for confirming the originality of the sent message. For example, if you send a file and you want to know whether it has been sent to an intended user without any change or not, then there’s the number of ways to check, like contacting the addressee or verifying the file and one of the approaches is also this hashing algorithm.
Let’s dig into the detail and understand: Hash Function & Hashing Algorithm.
Let’s move further and explore what’s hashing algorithm.
What is Hashing Algorithm & How Hashing Algorithm Work?
However, there’s no guarantee that the message will be in multiples of 512 bits. In some cases, a technique named Padding is used, where the whole message is divided equally in a fixed size of data blocks. The below example shows how the data blocks are processed.
- Fast to compute the hash value regardless of the data.
- Once hashing is done, it’s almost impossible to generate a message in its original form.
- Should be able to avoid hash collisions. For every message, it has its hash value.
- Even a small change should make a change in the entire hash value. Also known as the avalanche effect.
4. RACE Integrity Primitives Evaluation Message Digest (RIPEMD)
Expired Certificate Windows 10
Moreover, it’s also useful for the identification of the files, indexing of data in hash tables, detecting duplicate data, or as checksums to detect there’s no accidental or intentional corruption of data in the sent file. Lastly, for security purposes, it’s recommended to use hashing algorithms equipped with the newest technologies.